WIRELESS NETWORK PENETRATION TESTING
Most of the time, wireless network is deployed to enable Internet connectivity within the vicinity of coverage. With the help of wireless network, users can perform tasks given by communicating with others, getting resources from Internet, perform business transactions, etc. with the focus point of mobile at the same time.
In a business environment, the wireless network might contain critical gaps and vulnerabilities that could be used by attackers to leverage sensitive data transmitted in and out of the wireless network.
Weakness of a Wireless Network
Conducting a wireless network penetration testing can identify the weaknesses in a wireless network by using both automated and manual penetration techniques. Wireless network pen-test can help to locate and map authorized and unauthorized wireless access points, review corporate access point configuration, and then locate flaws that could allow an attacker to penetrate those networks.
Any potential risk in the network will be documented together with a recommendation plan. To minimize the potential risks detected, an ideal secured network solution will be designed to assist the client in creating a safer environment for their business process.
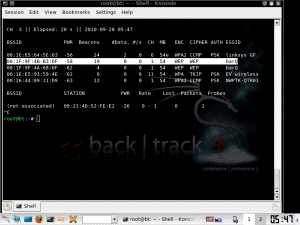
Wireless Network Penetration Testing cover activities such as testing the protective measures on different security protocols, WPA / WPA2 / WEP / WPS.

An actual wireless site survey report that illustrate wireless signal quality.


